
RAG TV – How Criminals Exploit Weak Signal Security
March 20, 2021 12:11 amRisk and Assurance Group Television S3E11 explores the role of signalling control in managing fraud and security in mobile networks.... View Article

Risk and Assurance Group Television S3E11 explores the role of signalling control in managing fraud and security in mobile networks.... View Article

Join Kaleido Intelligence and Cellusys for a free webinar addressing the current state of mobile network security and how Operators can ensure best-in-class protection from a world of evolving tech threats.

The Cellusys Steering of Roaming solution powers a unified approach to roaming for Telenor Group affiliates.

Nov 11-12 2020 – Virtual Event The topics for Thrive this year include Digital Resistance and 5G. This means protecting... View Article

Brendan Cleary is moving into the position of CEO and is now one of three executives that began their careers with Cellusys from university internships: John O’Hara will move into the position of COO, and Daniel McTague remains as CTO.

Cellusys Voted #1 Steering of Roaming Vendor in Independent 2020 Rocco Report Cellusys, a telecommunications solutions provider has been announced... View Article

Among all the good work that TSF does, one project for us stood out among others: mLearning for Syrian children.

Many operators seem to want it both ways: they want everyone to use SMS for 2FA, and reap the rewards in revenue - but at first sign of a security issue, the response is “SMS isn’t secure anyway.”

What is Diameter? Diameter is one of several defined Authentication, Authorization, and Accounting (AAA) protocols. What does that really mean?... View Article
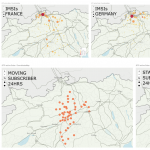
Coronavirus pandemic taxes crucial communication services globally Dublin, March 26, 2020 – Cellusys, a global mobile telecoms solutions company, is... View Article

With advances in Cellusys technology St Patrick had to change his message to the lucky four-leaf clover to take account... View Article

Customized Pricing “While companies may be tempted to focus on cost, as they have done for many years, the best... View Article

#4 Security Hackers and other bad actors are constantly seeking (and finding) new vulnerabilities in networks, and access points to... View Article

#3 Reliability In addition to switching between networks globally, eUICC technology also enables static devices or devices with a small... View Article

#2 Switching Downtime in IoT may refer to the time a device itself is inoperative, or to the time it... View Article

#1 Global Coverage Let’s skip the stats about how IoT is dominating, and will be affixed with the rocket booster... View Article

At the end of 2019 Ericsson estimated the number of 5G subscriptions to be only 12 million. Projections for the... View Article

IoT Vulnerabilities A Microsoft IoT study shows 97% of IoT adopters have concerns over security. Well, aren’t we all concerned... View Article

The Cellusys Signalling Firewall was first to market with a firewall for SS7, then with a firewall covering Diameter protocols... View Article

MOBILE OPERATORS Total Mobile Operators Revenue in 2020 is forecasted around € 1,275,000,000,000 (€ 1,275 billion). source: www.statista.com ROAMING REVENUE... View Article