5 Considerations When Choosing an IoT Connectivity Partner (4/5) – Security
#4 Security
Hackers and other bad actors are constantly seeking (and finding) new vulnerabilities in networks, and access points to data and devices.
“When companies are trying to determine how well connectivity providers can combat such intrusions, they should focus on three areas: infrastructure, endpoint security, and encryption techniques.”
We all “know” we need to think about security in our IoT fleets, but studies show that security is taking a back seat to production in the priorities of many enterprises. The start-up arms race rushes blossoming companies and their products through (or entirely around) crucial security planning.
Infrastructure
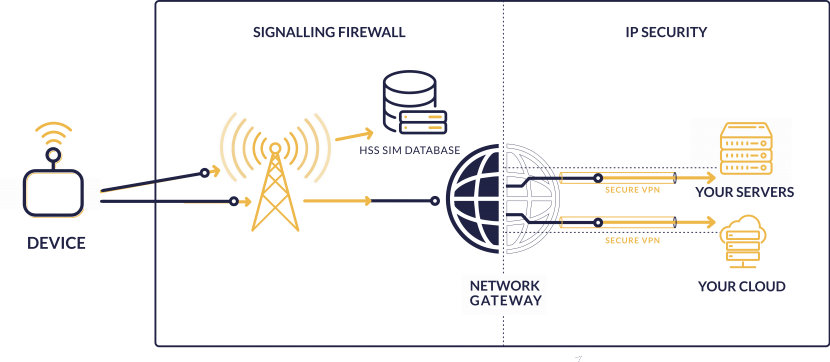
Security infrastructure includes both the IP layer as well as signaling security. Most connectivity providers use VPN tunnels and maybe even private APNs. This is the industry standard in security from the network gateway to the data center (private servers, and/or cloud).
Internet
The purpose of an encrypted VPN tunnel is to be sure data is never exposed to “raw” internet, where anyone may be able to gain access to sensitive information. However providers (and their customers) completely overlook the need to secure the mobile network infrastructure relied on to reach the gateway and VPN tunnel in the first place.
GSM (Mobile Networks)
Each mobile operator has their own security protocols and with this of course comes the inherent danger that they are not entirely protected. Many networks use signaling firewalls and comply with GSMA recommendations, but there are no guarantees that they rigorously maintain and update their firewall according to emerging threats or improved recommendations.
Choosing a connectivity provider that has expertise in signaling security as well as IoT is the only way to guarantee the highest level of safety for IoT devices reliant on signaling protocols.
Endpoint security

There are both physical and virtual elements attributable to endpoint security. Physical security relies mainly on how a device is protected out in the wild. A remote meter may benefit from a barbed wire fence, but all devices run the risk of being stolen or broken into. Physical security is a matter of protecting assets, but also of protecting your SIMs.
Embedded SIM (eSIM)
Stolen SIMs may cost an enterprise thousands in overages and roaming fees, or even just in data usage before they are able to pull the plug on the stolen SIM. The best way to prevent SIMs from being removed from a device and used in another is to hardwire it into the circuit board. eSIMs are more microchips than cards that can be permanently embedded directly in the manufacturing process. In this way, in order to hijack the SIM, someone would have to hijack the whole device. This is a drastic improvement from the removable SIM card we all recognize in our phone.

eUICC (Multi-profile)
The only challenge to using eSIMs is that unless they are eUICC, the device will be married to the network the SIM is programmed for. If it cannot be programmed OTA, the chip must be pre-programmed before assembly, and the device will be limited to using only the pre-programmed network. With a traditional SIM, the card can (and must) be changed if a different network is required. This means that a manufacturer that ships devices to several countries may need to divide their manufacturing processes by destination, and if the network becomes unavailable in the future, or the device migrates to a new location outside the home network, the device itself becomes somewhat obsolete.
APN Authentication
The other virtual aspect of endpoint security is the access point name (APN) and virtual private network (VPN) setup. APN is essentially the gateway that authenticates and allows a device to connect directly to the internet over the mobile network. By requiring an individual username and password to connect to the network, SIM hijacking can be prevented. A VPN encrypts the data itself to ensure it cannot be intercepted by third parties. Generally speaking, the tighter the access to the APN or VPN, the less likely someone may gain access to an endpoint device.
An eUICC enabled eSIM is the best way to ensure endpoint security while maintaining future-proof connectivity.
Encryption techniques
Encryption mainly refers to the encryption of data packets through VPN tunnels as mentioned before. Complex algorithms should be used to provide improved protection against data interception as simpler algorithms are increasingly cracked. There are various kinds of VPN tunnels, however IPsec provides the most advanced standard of encryption allowing for a secure connection from the device itself to the data center (cloud or server). A VPN combines encryption with hashing and authentication techniques to ensure data can travel safely from the device over internet protocols without interference or interception.
Encryption may also be built into the software or firmware of the device itself (much like Whatsapp or banks utilize encryption), however this is specific to the manufacturer or software provider and cannot be influenced by the connectivity provider.
As risks continue to evolve, security cannot be an afterthought in IoT. Choosing a connectivity provider with expertise and dedication to security adds value to your brand and protects your investment.
Tags: APN, endpoint security, eSIM, IoT security, VPNCategorised in: Blog
