Anatomy of the Flubot attacks – Flubot and Smishing Solutions Part 1/7

What do Flubot and SMS phishing have in common? Shocking daily headlines, the Wild West of URLs, and one easy solution to stop both in their tracks.
If you have heard anything about the newest Flubot attack, you have probably also warned your parents and others not to trust or click any link from an SMS message. This is bad news for MNOs. Fraud has been on a steep incline since the COVID-19 pandemic began, and consumers, while under attack from the virus, are also under attack electronically and financially.
Smishing, malware, and the Flubot are dominating headlines. These attacks may seem like separate threats, but they have a lot in common: They both begin with an SMS message and end in devastating financial losses to subscribers. Mobile operators have responded by issuing warnings to consumers, yet they are missing an enormous opportunity to save the day and savour the glory (and press coverage) any hero should.
Anatomy of the Flubot attacks
We will describe the most common Flubot attacks currently seen, however the companies, industries, and other details about the content and technique of the attack are sure to evolve and spread. Although this is currently accurate, it can be considered an example of a Flubot attack, as many possibilities and variations exist.
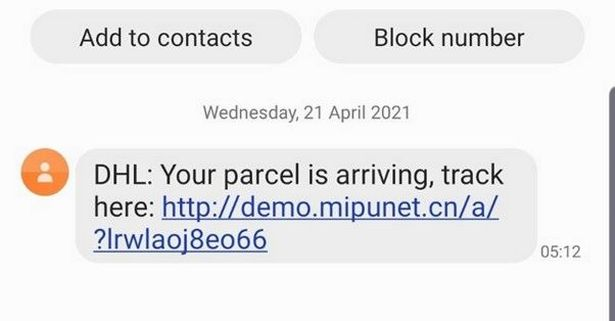
An attacker sends an SMS with a claim about an undelivered package, or a problem with a bank account. They also frequently utilise SMS spoofing (falsifying the sender party ID) to make the message appear more credible. This means that the message will appear in the same thread as previous messages from a legitimate sender. Frequently these messages are sent in high volumes (spam) but this is not always the case.
The message, purporting to be from a bank, delivery service, or other trusted entity includes a link to their website to resolve the problem. This link may lead to a website domain that was only purchased the same day, or even a legitimate domain with some kind of corrupted page, or user hosted content section (such as github). The page is styled to look like the DHL or bank website and convincingly prompts the user to download a fake look-alike app (such as the DHL tracking app). However, this is not any normal app; it is an APK file, which is a kind of 3rd party app, not vetted by the Google Play store. It could contain just about anything.
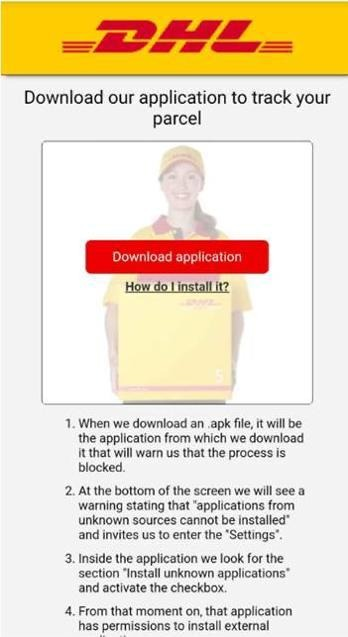
The instructions ask you to change some settings in your phone to allow external apps, but this does not specifically require the user to change their “security” settings. If you follow the instructions (as many do) and download the app, you will get much more than you bargained for, The app is a trojan for malware, that is now able to access sensitive data including your banking details, etc, by overlays to sit above website browser windows, recording keystrokes, collecting typed data and credentials.
To add insult to injury, the Flubot may also access your contact book and send SMS text messages to anyone and everyone in your directory in order to propagate itself. Imagine your phone taking a big infected sneeze all over your friends and family.
The attackers now have enough of your private data and credentials to empty your bank account, steal your identity, and destroy your life as you know it. You can get the malware off your phone, but the damage is done.
Proofpoint suggests that Flubot has spread to the UK, Germany, Hungary, Italy, Poland, and Spain. The Flubot has already collected 25% of Spanish mobile numbers, affected over 60k devices, sent millions of messages, is present on “all networks” according to Vodafone and shows no signs of slowing.
Operators have responded by issuing statements warning the public of the new scam, and less publicly suggesting that the responsibility for this epidemic lies with Google and the Android operating system for allowing a workaround to download unapproved apps in the first place. The speed and complexity of this attack make it a tough knot to untangle, and as of yet no operators have offered a solution.
More information on the Cellusys SMS Anti-Phishing Solution
How SMS Anti-Phishing works:
The SMS Anti-Phishing Solution can be used in conjunction with an SMS firewall or as a standalone solution for SMS phishing and Flubot attacks.
Every SMS is checked for the presence of a URL. Cellusys authenticates every URL against the Phishing Threat Intelligence Database registry. Even if the URL redirects multiple times across multiple domains, the destination URL will be authenticated:
The subscriber receives the message in one of three ways:
- Verified Safe URLs: Subscriber can open the link
- Potentially Dangerous URLs that cannot be verified: the link is replaced with a redirect link to a warning page explaining why the page is blocked, and urging the subscriber only to open with extreme caution.
- Dangerous URLs that are known: the link is replaced with a redirect link to a warning page explaining why the page has been blocked.
More Information about Fraud Insight solution for Malware
Sources:
https://therecord.media/massive-flubot-botnet-infects-60000-android-smartphones/
https://www.walesonline.co.uk/news/uk-news/o2-issue-urgent-scam-warning-20467000
Tags: Flubot, flubot solution, malware, smishing, trojan, zero trustCategorised in: Blog
