Is There a Cure? – Flubot and Smishing Solutions Part 6/7
What do FluBot and SMS phishing have in common? Shocking daily headlines, the Wild West of URLs, and one easy solution to stop both in their tracks.
If you have heard anything about the newest Flubot attack, you have probably also warned your parents and others not to trust or click any link from an SMS message. This is bad news for MNOs. Fraud has been on a steep incline since the COVID-19 pandemic began, and consumers, while under attack from the virus, are also under attack electronically and financially.
Smishing, malware, and the Flubot are dominating headlines. These attacks may seem like separate threats, but they have a lot in common: They both begin with an SMS message and end in devastating financial losses to subscribers. Mobile operators have responded by issuing warnings to consumers, yet they are missing an enormous opportunity to save the day and savour the glory (and press coverage) any hero should.
Is there a cure?
Arguably, yes. Let’s think in terms of a vaccine, and a treatment. Verifying the integrity of every single URL in every single SMS sent to subscribers is the fastest way to stop both Flubot and smishing in their tracks. For users and networks already affected by malware, there is a way to test and identify infected handsets, and thereby alert subscribers to the infection and help them to purge the malware from their device.
The vaccine – SMS Anti-Phishing
The ounce of prevention worth a pound of cure: Assume every URL is dangerous unless authenticated as safe. A URL verification approach to all URLs delivered through SMS messages is enough to stop smishing and malware from infiltrating your network and wreaking havoc on your subscriber base. None of the security solutions we’ve discussed get the solution wrong – however none are complete or robust enough to truly protect subscribers from these attacks. SMS Anti-Phishing ensures that every URL sent to every subscriber is safe and secure.

Imagine a world where there are no victims that fall prey to a phishing site in the several days before the site is reported as fraudulent and shut down. Malicious links are blocked and potentially dangerous links that have not yet been classified are delivered with a strong warning. Consumer education is an important component to protect against phishing, however the reach of tweets and press releases are not enough. Mobile operators are in a unique position to inform their subscribers about the veracity of every single link, directly to their phone, exactly when they receive it – and be the hero of this story.
Imagine that while subscribers in competing networks are bombarded with messages not to trust links in SMS messages — no matter the sender — your subscribers are informed with every single URL they receive, which links are safe to open, and which links have been blocked for their security. Communicating real security messages to the subscriber on a daily basis, deepens the trust the subscriber has in the network, by reinforcing the network’s ability and commitment to the customer’s safety. This, in turn, restores their faith in SMS messages in general, which results in higher open rates and higher conversion rates of A2P messages.
The Test and the Treatment – Malware detection
Obviously, the priority to stop this devastating e-plague is to stop the malicious links that lead to fraudulent websites in the first place, however if Flubot is already suspected on a network, steps to control and contain the damage must also be considered. Malware is usually invisible to the consumer, meaning that users who are now in the process of being victimised, may also be completely unaware of it. More than 1 in 100 mobile devices is infected with active malware even without the Flubot epidemic going around. This is another unique opportunity for mobile networks to save the day for their customers.
Using powerful broadband analytics and deep packet inspection, all devices on the network can be scanned for malware, viruses, and trojans without the need for downloading apps or any other interaction at the subscriber or device level. As an immediate remedy to the Flubot outbreak, the operator can issue a warning to infected subscribers with instructions about how to remove such malware from their device. Alternatively this can be an extra or optional security service the user subscribes to.
Malware and virus detection can also be used as a way to determine the extent of the impact, and detect and stop new attacks before they are able to run amok.
More information on the Cellusys SMS Anti-Phishing Solution
How SMS Anti-Phishing works:
The SMS Anti-Phishing Solution can be used in conjunction with an SMS firewall or as a standalone solution for SMS phishing and Flubot attacks.
Every SMS is checked for the presence of a URL. Cellusys authenticates every URL against the Phishing Threat Intelligence Database registry. Even if the URL redirects multiple times across multiple domains, the destination URL will be authenticated:
The subscriber receives the message in one of three ways:
- Verified Safe URLs: Subscriber can open the link
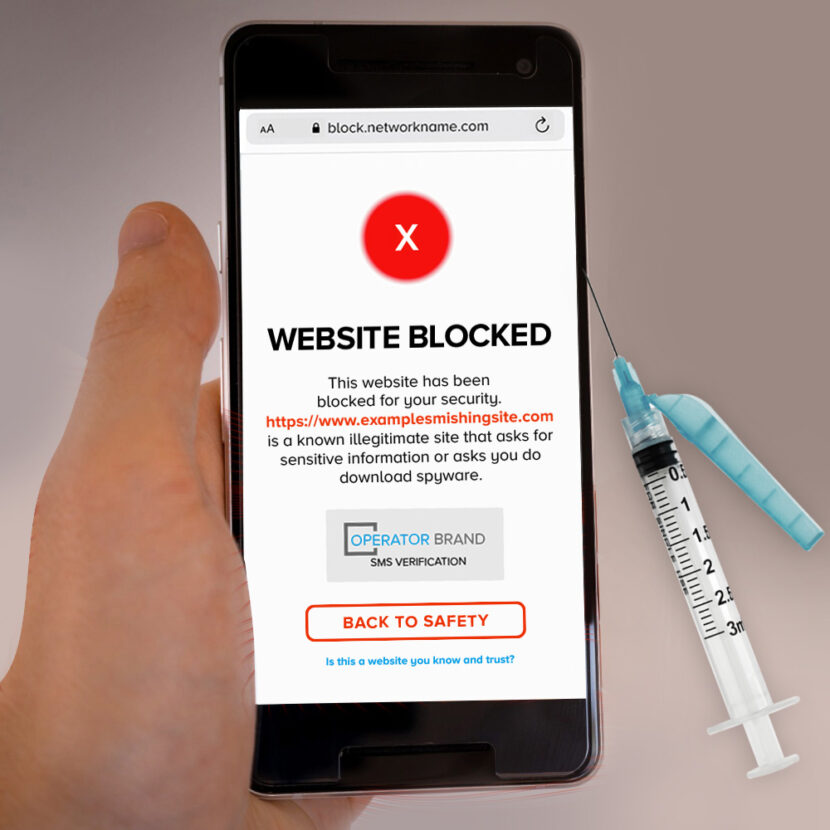
- Potentially Dangerous URLs that cannot be verified: the link is replaced with a redirect link to a warning page explaining why the page is blocked, and urging the subscriber only to open with extreme caution.
- Dangerous URLs that are known: the link is replaced with a redirect link to a warning page explaining why the page has been blocked.
More Information about Fraud Insight solution for Malware
Sources:
https://www.ncsc.gov.uk/guidance/flubot-guidance-for-text-message-scam
Tags: Flubot, flubot solution, malware, smishing, trojan, zero trustCategorised in: Blog
