Flash calls: New Authentication Channel For MNOs
This blog from Cellusys, written for mobile operators, outlines the emergence of Flash Calls and how they can be detected.
What are flash calls?
A Flash Call is a way of authenticating a user using a mobile device. Just like the (perhaps) more familiar One Time Password (OTP) via SMS. A Flash Call is essentially a zero-duration or dropped call placed to the mobile device. Where a part of the calling number acts as the OTP code. On many mobile devices, this code is processed automatically. The user is then seamlessly authenticated into the app or service in question.
Enterprises have (for some time now) enjoyed the ubiquity, security and affordability of SMS. But the latter is under pressure due to exploding SMS termination pricing. Hence some firms have moved to flash calls. These firms now benefit from a reasonable level of security for reduced costs as compared to SMS.
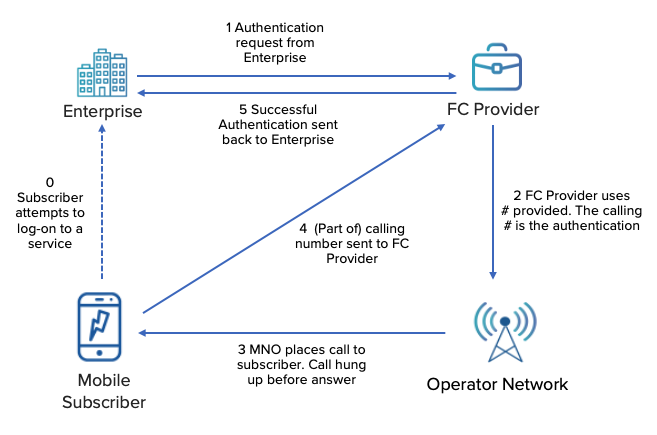
However, as happens often with new technologies, the regulations and the end-user acceptance of such take time. Mobile operators do not get paid for zero-duration calls – and subscribers may not be expecting authentication via a call.
However, some MNOs are more willing to protect their existing application-to-person (A2P) SMS revenues. Whereas other MNOs are happy to harness the opportunity of this new revenue stream.
Leaving aside the divisive nature of flash calls within the global telco industry. Mobile operators cannot control what they cannot see. Hence any service which provides flash call verification and detection is both welcomed and necessary.
The market landscape of flash calls
There are a number of large global CPaaS players who provide flash calls. As well as many smaller, more specialised firms. The former tend to have multiple means to authenticate a user, such as SMS, flash calls, and email. In contrast, the latter might be nimbly responding to changes in the authentication landscape. They focus solely on flash calls for authentication.
A flash call, however, only really works effectively on Android handsets. This is due to the operating system (OS) that needs to allow the smartphone application to access the phone logs – which iOS does not support. Hence, Apple users will have an incomplete or otherwise poor authentication experience. Therefore, firms seeking to authenticate users across a broad range of handsets should be aware of this limitation, and provide a range of options for user choice.
This poses challenges for MNOs. Traditionally, 4% to 8% of MNO revenues come from A2P SMS, but this revenue stream is now threatened. MNOs are increasingly seeking to incorporate flash call capabilities into their A2P monetization services. Most service requests coming from MNOs in the past 12 months tend to include this. However, this is not within the remit of a SMS Firewall but rather a Voice Firewall, since flash calling is placed on a voice trunk. Traditional SMS Firewall vendors may struggle to include this in their offers. This is where a multiprotocol signalling firewall comes into play. As outlined previously, in order to take any action on flash calls, you need to perform flash call detection. It’s only with the insight given by efficient and robust detection systems that MNOs can then perform further actions. Such as blocking, disrupting or indeed flash call monetization.
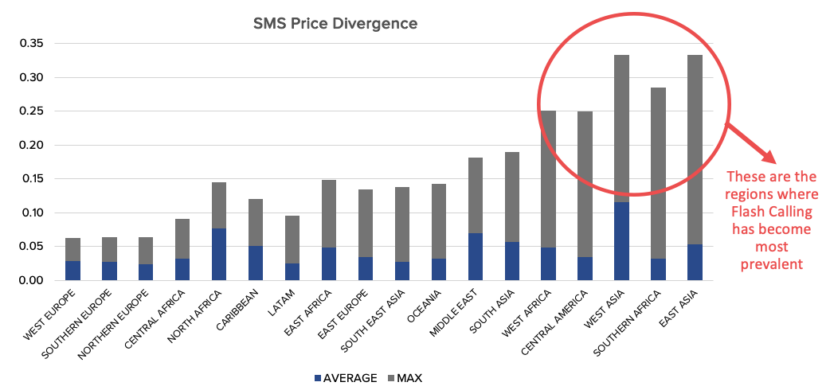
As Figure 2 indicates, the regions where there was a huge increase in SMS termination costs, were the first to witness some firms move to flash calls for their authentication. As the leading SMS analyst MobileSquared reports, the average global price for an SMS increased from $0.033 to $0.6495 between 2021 and 2023.
How can MNOs detect flash calls?
Detecting flash calls has proven difficult because most firewalls can’t discern genuine OTP flash calls from fraudulent practices. These rely on dropped calls, such as Wangiri, or indeed from genuine zero-duration calls placed by customers. Furthermore, the same calling line identifier (CLI) is rarely reused, given the very nature of flash calls, making CLI spoofing another challenge.
In a post-processing CDR based solution, the call duration can provide additional context. However, even if a flash call can be detected after the fact, the CLI will never be reused. This post-fact knowledge becomes redundant and is generally an ineffective way to detect flash calls.
Among other call parameters to analyse :
- CLIs for length
- CLIs conformance to a valid international numbering plan
- Call durations
- Calls from repeated numbers or number ranges
- Short call durations from similar number ranges
Cellusys Voice Firewall: a simple flash call detection solution
Cellusys Voice Firewall provides real time visibility into calls and the capability for total control over them.
The system is built on the Cellusys Signalling Control Platform. This platform supports applications such as the Signalling Firewall and SMS Firewall. Therefore, the Voice Firewall benefits from the same baseline functionality and advanced reporting capabilities provided by the signalling control platform.
The Cellusys firewall doesn’t rely on call detail record (CDR) processing like some other solutions. Instead, it focuses on processing signaling related to voice call setup and management. The Cellusys Voice Firewall acts as a single point of visibility for the network. It records all calls in one place and ensures consistency.
In many networks, the control of calls is divided across different nodes in the network, such as the HLR, MSC or the Fraud Management System (FMS). This makes it difficult to efficiently take immediate and consistent action based on call analysis. However, the Cellusys Voice Firewall system solves this problem. It can act as a single point of control. Cellusys knows and understands the myriad core-network implementations in the field, so this flexibility is afforded by a range of APIs.
Flexible integration across CAMEL, INAP, SIP and ISUP is key. Covering voice calls of all types, however they enter the network. Furthermore, since both Flash Calls and A2P SMS are the two most popular ways of authenticating users over mobile networks, it stands to reason that a firewall solution incorporating voice and signalling is optimal.
Cellusys Voice Firewall uses in-house-developed mathematical models and algorithms to analyse the call parameters presented above, and many more, in real time. The Voice Firewall is constantly gaining additional knowledge by processing millions of calls daily. So the accuracy of detection, recently rated at 99.6% in a live network in MEA, keeps improving.
Key takeaways
To gain full visibility and establish control on what traffic crosses a mobile network , an effective voice firewall must be part of a comprehensive platform featuring an SMS firewall and a signalling firewall..
Cellusys Voice Firewall answers the demands placed on MNOs by ever-evolving omnichannel authentication procedures by:
- Flexibly integrating across all network protocols in a multitude of network settings
- Working in real-time on the signalling that establishes, maintains and takes down voice calls
- Working alongside the Cellusys SMS and Signalling Firewalls
Contact us for a demo of our voice firewall to see how you can protect your network and detect flash calls.
Tags: A2P SMS, CLI spoofing, Flash Call Detection, Flash calls, monetization, OTP, security, Wangiri