Home » dubai » Introduction to Diameter Signalling Controllers
Introduction to Diameter Signalling Controllers
Hi. This is Chuck Wesley-James, from Cellusys.In this presentation, we are going to look at Diameter Signalling Controllers (DSCs) and what they do in a Telecom network.
We are going to make the assumption that you have some knowledge of the SS7 network, so that we can compare the Diameter Network with SS7.
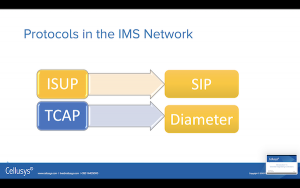
Let’s take a look at some protocols involved. In 2G and 3G core networks, we used SS7 and two sub-protocols called ISUP and TCAP. In LTE or 4G, the core network is called an IMS network, and the ISUP and TCAP have been replaced by SIP and Diameter.
ISUP did the job of setting up the phone call. It made the far-end ring and set up the circuit switches. In the IMS network that job has been moved over to a protocol called SIP (Session and Initiation Protocol). You’ll be using that if you’re doing voice over LTE (VoLTE)
Now back on the 2G and 3G side, TCAP took care of a little higher level of a control. It dealt with getting you authenticated onto the cell phone network. It determined if you could roam and what services you to have. That protocol has been displaced by Diameter, so in the LTE/4G network, you will have Diameter doing the same functionality.
A few more details….
4G or LTE really has two backend networks: EPC and IMS, but that distinction isn’t needed in this short video. The EPC and IMS make use of two key signaling protocols in the core network:
- Session Initiation Protocol (SIP) used within the IMS for setting up sessions.
- Diameter used in both EPC and IMS for transactional events (requesting information).
Diameter is an IETF defined protocol originally designed for Authentication, Authorization, and Accounting (AAA) as an improvement over a protocol called RADIUS. Diameter improved on RADIUS by supporting:
- Improved failure handling
- More reliable message delivery
- Bigger information elements
- Improved security
- Extensibility
- More flexible discovery of other nodes.
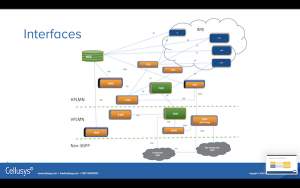
These are the interfaces that are using the IMS/EPC core network. For each of these interfaces, the diagram gives the network elements in the EPC/IMS network and labels the interfaces between them.
Rather than referring to an interface as between the HSS and the SGSN, we call it the S6a interface. It is sort of confusing to have to memorize these names, but that is what the industry uses.
Let’s take a look at a few of these interfaces:
Gy and Gx interfaces are a little special, they’re kind of unusual, and there’s a whole video on those, along with S6a. https://www.youtube.com/watch?v=8YCufy6nW-8
If you’re roaming then the S9 and the S6d interfaces are pretty important.
Let’s face it: This diagram is pretty complicated, there’s a lot of connections and we’ve even simplified this diagram because really in your network you’re going to have a whole lot of MMEs. This is why you want to start looking at having Diameter Signaling Controller. It simplifies all these connections.
Next, let’s take a look at why you want to simplify these connections.
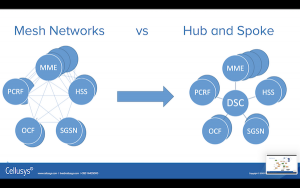
Leaving the previous complicated diagram, let’s take a look at the purpose of the DSC or a Diameter Signalling Controller.
If you don’t have a DSC you are going to end up with a network shown on the left-hand side. It’s actually going to be even more complicated than this; it’s a mesh network. That means pretty well everything has to get connected to pretty well everything else. If you were to add a new HSS on to this diagram you’d have to have every MME connect to that new HSS. This is an Operations nightmare.
There’s just far too many connections to maintain. It also means you’ve probably got very little security on here and you certainly have no one place to go to take a look at where the traffic is flowing and how much. It is pretty hard to tell if too much traffic is taking place or if one node is carrying too much traffic. It also means you probably can’t connect to another carrier for roaming because you certainly wouldn’t want other carriers connecting directly to your HSS and directly to your PCRF.
It also means in this you’ve got a terrible network to troubleshoot.
Mesh Network
- Operations nightmare
- Far too many connections
- New HSS implies modifying every MME
- No Security or Central Traffic view
- Terrible Troubleshooting
You need a central place to mange your network, which is what a DSC is going to do for you.
So let’s simplify this mesh network, by putting DSC in the middle. If you come from SS7 background that DSC looks a lot like an SS7 STP. In SS7, the STP takes all the messages decides where to route them and send them out again. This is done in a hub-and-spoke architecture just like we’re showing here.
Like an STP or even an IP router, the DSC, turns a mesh network into a hub an spoke pattern.
This means that
- One place to make connections. For example, a new HSS node requires only one connection, saving you doing a modification in every MME
- One place for value-added processing like Signaling Firewalls or Billing
- One place for external entities to access your network – a DEA…. You would not want another operator connecting to your MME…. Especially not hundreds of other operators.
- One place for troubleshooting
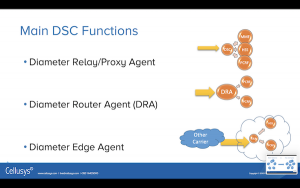
Let’s take a look at the main functions of the DSC, and what people are going to be talking about.
Relay or Proxy Agent:
If you started learning about the DSC from the standards, you would have read about the relay or proxy agent. It is the base definition of a DSC. When a message comes into the DSC, it’s going to be from some node like an MME or HSS, and it is going to be sent to another node like a HSS or PCRF.
Most of the messages actually have a destination host and a destination realm, so the DSC’s job is pretty darned easy.
The difference between relay and proxy is simply that a proxy is allowed to change the message somewhat, but when you’re out shopping for a DSC that’s not going to come up in conversation: any decent DSC is going to be able to both Relay and Proxy functions.
A Diameter Routing Agent (DRA) is something else, and it can be pretty expensive, so let’s be sure of what we are talking about.
If you look at the standards for a DRA, you will see it is NOT a Core Router. It is something that specifically sits in front of a group of PCRFs. We tend to get lazy we talk about DRA’s as core routers, doing what we described in the Relays and Proxys, but the strict definition of the DRA is only in front of PCRFs.
A DRA routes messages to specific PCRFs based on something called an IPCAN session. (Here is a video that goes in to more detail on DRAs and IPCAN sessions: https://www.youtube.com/watch?v=8YCufy6nW-8 . ) Depending on the smarts contained within your PCRF, you might not need a DRA. If your PCRF is running hot standby or multiple PCRF nodes are sharing the IPCAN session data you likely don’t need this functionality.
DRA functionality tends to be expense, so ensure you actually need one before you go buy one. Otherwise stick to the basic DSC functions.
The Diameter Edge Agent (DEA), is a basic function of most DRAs, just like Relay/Proxy, but it does have more smarts.
The Diameter Edge Agent is the place where other carriers are going to connect. You don’t want other carriers to connect their MMEs and other nodes directly to your nodes. Operationally – it’s a mess. Security wise – it’s a complete mess.
So the Diameter Edge Agent’s job is to let the other carriers access your network functions in a controlled manner and to do some basic security. In the SS7 world, this would be called Network Gateway STP. Commonly carriers have one STP doing internal routing and acting as the Network Gateway. Similarly the DSC can also do internal routing and act as the DEA.
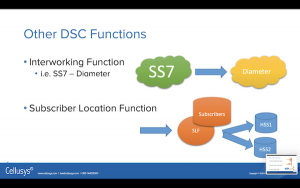
There are a couple other functions you might hear about.
The Interworking Function (IWF), which is typically between SS7 and Diameter. You might hear about it, but the commercial use cases for this are not great. There are not a lot of IWFs in the real world. If you carefully go through the use cases, and the functionality required in your SGSN and/or HLR, you will probably find won’t need this in your network.
The Subscriber Location Function (SLF) is a diameter proxy agent or relay agent, which looks up list of subscribers in your network and then determines where it’s going to send the message. You might need this if got an HSS and you’ve got so many subscribers you have to divide it to multiple HSSs: Here an SLF will help.
SLF functionality is really only used by the absolute largest carriers. They have huge number of subscribers, forcing them to use and SLF. But if you are a smaller carrier and you don’t need to maintain this extra list of subscribers on the SLF then don’t do it.

Let’s get back to the Diameter Edge Agent (DEA), because it’s pretty important.
A Diameter Edge Agent often works with a Signalling Firewall. A DEA typically has some security built into it, but security functions are going to get much more in depth when you work together with a Signalling Firewall.
The Signalling Firewall can sit directly on the Diameter links, or it can be a value-added feature on top of a DEA.
The DEA takes care of basic message routing. It knows about destination hosts, destination realms and routes messages. It can do some things like topology hiding. (If you’ve seen my other videos, you will know, I’m not too impressed with Topology Hiding as a security feature. https://www.youtube.com/watch?v=wRYetUZgdqU ) The DEA will take care of things like IPSec and DTLS to secure those connections and understand who they are. The DEA deals with that nodal connectivity. That’s its job, it’s a DSC at heart.
If you are using the Signalling Firewall as a value added feature on the DEA, then we want the DEA to do is to send a subset of traffic to the Signalling Firewall. We want the DEA to send any of the traffic that’s going to come into your network, because that is traffic upon which, we want the Signalling Firewall to do some extra checks. Maybe the messages that are going between your own MMEs and your own HSS you don’t want to send to the Signalling Firewall or you just want to check for throttling to make sure they’re not sending too much traffic.
So you’ve got a lot of traffic choices you can make and the DEA is going to be able to determine which messages will go to the Signalling Firewall.
Let’s take a look at the Signalling Firewall and what it is doing.
The Signalling Firewall is one central place for all the security rules about what messages are going pass through your network.
You could have some rules for this in the DEA, some in the HSS, and some in the PCRF, but when you come to troubleshoot your network, or question why a given message was allowed through, you have a head ache. When you come to troubleshooting, to determine why you have blocked a message you would have to look in four different places. That’s not good.
The Signalling Firewall should be the central place for all the rules. It needs to be able to provide some pretty exacting reporting and logging of what messages it drops and for what reasons. It is also one central place for all the protocols, because we know diameter is not the only protocol on your network. You’re probably also running SS7, maybe SMPP for your SMS messages and GTP. You can use the Signalling Firewall to act for all those protocols at one time, using the same database.
This will allow you to do per country and per carrier analysis and much better, because it’s one central place to look at all the data, regardless of what protocol was used.
The main function of the Signalling Firewall is to protect your network. Using rules to distinguish the messages, the Signalling Firewall is then going to Ignore the message, or Return an Error or Modify the message. The first step is to define those rules to find fraudulent or errant messages. The GSMA specifies category 1,2 and 3 messages, and this is a good place to start, but not the end.
Category 3 messages are a little special. For these messages the Signalling Firewall needs to know some information about the subscriber before determining the validity of the message. Unlike a DEA, the Signalling Firewall can query the HSS, VLR or handset for that subscriber information before it makes a determination.
So the Signalling Firewall is pretty sophisticated on what it can do and it maintains lot of rules and past data. It is the place that brings together rules and protocols, to be one central place for troubleshooting.

During this presentation, I mentioned a couple of other videos. These are the links to them.
The first video will tell you about the Gx, Gy, and S6a interfaces. It explains in more detail what a DRA does with IPCAN sessions and why you might not really need a DRA.
The second video focuses on Diameter Security and how we haven’t really gotten any more secure from our SS7 days.
I hope you enjoy them.
Thank you for watching this video. I hope you have enjoyed it.
Please keep watching this space, as I plan to add more videos soon.
Categorised in: Blog
