Subscriber Identity Disclosure: How an attacker can obtain IMSI of a subscriber?
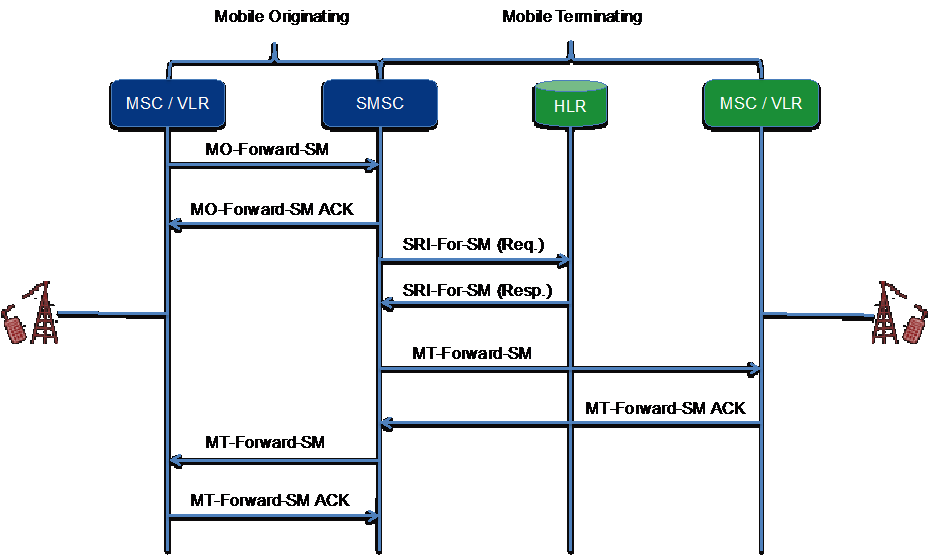
Since the “Subscriber Identity Disclosure” uses a portion of the Short Message Service (SMS) capability a brief explanation of SMS call flow is in order.
When a subscriber sends an SMS Message it is transported over the air interface to the base station. The base station then sends the message to the serving Mobile Switching Centre (MSC). The serving MSC embeds the message in a MAP Mobile Originating Short Message Transfer message (MO-Forward-SM) and sends it to the Short Message Service Center associated with the MSC. A subsequent acknowledgement is sent from the SMSC to the MSC indicating the SMSC receipt.
Since the SMSC does not know the location of the terminating subscriber – the SMSC requests this information from the Home Location Register (HLR) containing the information pertinent to the terminating subscriber. This is accomplished using the MAP-Send-Routing-Info-For-SM query message (SRI-SM). The terminating subscribers’ Mobile Station International Directory Number (MSISDN) is included in the SRI-SM to be used in the HLR query.
After the HLR lookup – the HLR returns an SRI-SM response to the requesting SMSC. At the MAP level this message includes the:
- Global Title of the current MSC/VLR serving the requested subscriber.
- International Subscriber Mobile Identity (IMSI) of the targeted Subscriber
After the receipt of the SRI-SM response – the requesting SMSC would use a Mobile Terminating Short Message Transfer message (MT-Forward-SM) to send the SMS message to the MSC/VLR currently serving the terminating subscriber.
The previous explanation was not meant to be an exhaustive study of the SMS process but rather an overview and a lead in to the use of the SRI-SM sequence to fraudulently obtain network and subscriber information.
Short Message Service Call Flow
Purposes of Attack
- Obtain IMSI of a subscriber
- Get address of MSC/VLR currently serving the target subscriber
Requirements For Attack
- SS7 Network Access with a route to the subscribers home network – fairly easy to obtain
- SS7 message generation capability – open source and easy to obtain
- MSISDN of target subscriber
Threat Setup
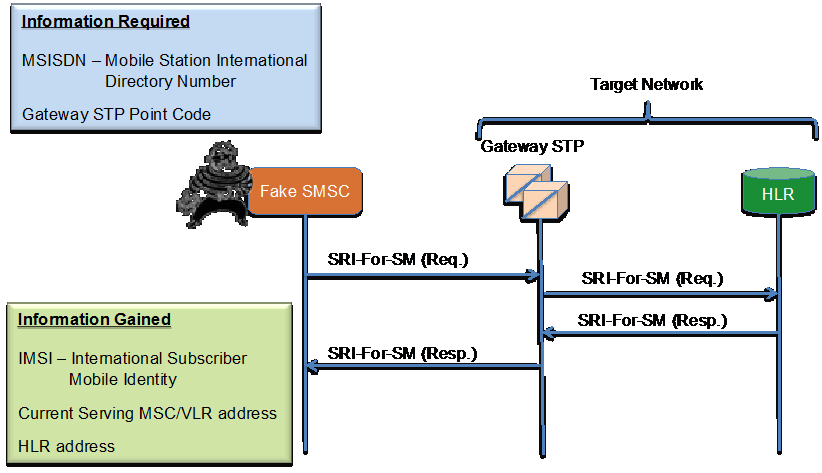
Attack Message Flow
In the scenario the intruder is posing as an SMSC wishing to deliver an SMS message to a subscriber. To deliver the SMS message the “Fake SMSC” requires the address of the MSC/VLR currently serving the target subscriber.
The “Fake SMSC” constructs an SRI-SM request message and includes the MSISDN of the target subscriber. Since the intruder does not know the address of the HLR in question – they use the MSISDN as the SCCP called party address. The intruder’s address will be placed in the SCCP calling party address field. The message is then routed to the subscribers home network where it is then routed to the HLR serving the subscriber. The HLR queries its database using the MSISDN as the key. The query results are placed in an SRI-SM response and sent to the Gateway STP for routing back to the originator of the SRI-SM Query.
Subscriber Identity Disclosure Call Flow
Results of Attack
The intruder currently has the following as a result of the attack:
- MSISDN of Subscriber
- IMSI of Subscriber
- MSC/VLR currently serving Subscriber
- Address of HLR in Subscribers home network
Collecting this information is the base for more attacks like “Track the subscribers location” and “Set up a man in the middle attack to listen in on calls”.
Solution
Signalling is the core of mobile networks and signalling attacks threaten network stability and subscribers security. Thus, Mobile Operators looking for suitable solutions for monitoring and analysis of signalling traffic to decrease the risk of revenue loss.
Cellusys Security Solutions provide network operators and their customers, with state-of-the-art systems to identify and prevent security problems in the overall Signalling (SS7, SigTran and Diameter) and Short Message Service (SMS) domains.
We will discuss more attacks in near future. Watch Cellusys Blog and LinkedIn page to know more about the possible attacks that threaten your network.
Categorised in: Blog