Penetration Testing by umlaut
Interconnection security as a
Service
Easy. Continuous. Automated.
Continuous, independent penetration testing is fundamental to a comprehensive security strategy for any network.
- Regular tests without setup costs
- Lower testing operational costs
- Closer to zero-day evaluation
Risks Monitored:
- Traffic interception (e.g., SMS, Calls)
- Subscriber/device tracking
- Denial of Service of a user or the entire network
- Impersonation of a subscriber. Identity spoofing
- Profile manipulation (Fraud, Revenue Loss)
Benefits:
- Easy to setup tests and analyze results
- Security scoring
- Regular testing with short time to results
- Integration with SOC /SIEM
- Covers most known risks
- SS7, GTP and Diameter
- New vulnerabilities added regularly
- Technical workshops included
- Protection of target SIMs and data
Autonomy for operators to:
- Assess security level
- Verify mitigations
- Fine tune rules set definition
- Validation in short time

umlaut Managed Service :
- Connection setup and troubleshoot
- Manual results validations
- Provide detailed countermeasures
- Follow-up mitigation action plan
- International security benchmark
How does Intaas work?
Setup & requirements
- Traffic is routed via the International network
- Intaas needs be configured as a roaming partner
- IR.21 is configured by umlaut in the customer interface
- SIM cards setup locally (home network)
Regular & Ad-hoc
- Ad-hoc tests can be performed immediately or scheduled (e.g. overnight)
- Tests can be performed regularly (weekly, monthly) and results integrated with a SIEM tool
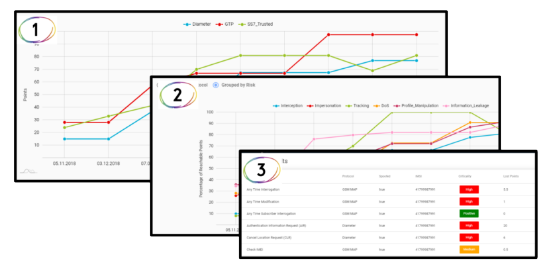
Result Analysis
- Protocols security scoring
- Risks-based scoring
- Detailed results per test case
- Network traces available
- Export to Excel / CSV
Interconnection protocols
- SS7 / Diameter / GTP
- Continuous improvement of test cases
- Only well-formed requests
- GSMA and beyond test cases
- GSMA FS.11, FS.19 and FS.20
- Tweaks and bypass techniques
- Limited to well formed messages
Trust It

Privacy and data protection
- Storage and processing is done on European Union based infrastructure
- Data retention can be set by the customer (default is 6 months)
- Dedicated database schema
- Multiple user roles concept
- GDPR compliant
Control of Target
- Only operators can use the tool
- Operators can only target their network
- Only MSISDNs / IMSIs from the operator’s range can be targeted. Ported MSISDNs can be set
- Target SIMs are notified via SMS
- Customer admin is notified once a new target SIM is configured
Why umlaut?
• umlaut has 15 years of experience in
telecommunication security assessments
• umlaut is active in multiple industries (e.g., automotive,
energy, aviation) which provide experience on services
and criticalities on those industries
• umlaut portfolio covers end-to-end: from
smartphones, IoT devices, air interface, backhaul,
core and services testing
• umlaut has a team of experts for network
engineering and testing
• umlaut has performed security assessments
with all equipment vendors
• umlaut participates in security groups (e.g.,
GSMA Fraud and Security
Certifications
• ISO 27001 – Information Security
• ISO 17025 – Testing and Calibration of Laboratories
• ISO 9001 – Quality Management
• Our consultants are certified on eg:
• Certified Ethical Hacking (CEH), ISO 27001 Lead Auditor, ISACA
CISA, CISSP, …
• Continuous partnership with 50+ operators, vendors and
industry partners for active security testing, training and
consulting services
• Groups of operators use our data for security
benchmark
